Fundamentals and Principles of Zero-Knowledge Proofs (ZK Proof Fundamentals)
This lesson introduces the core concepts, technical principles, and major types of zero-knowledge proofs, helping learners understand how ZK enables verification without exposing data, a foundation for later application chapters.
What Is Zero-Knowledge Proof?**Why ZK Matters**
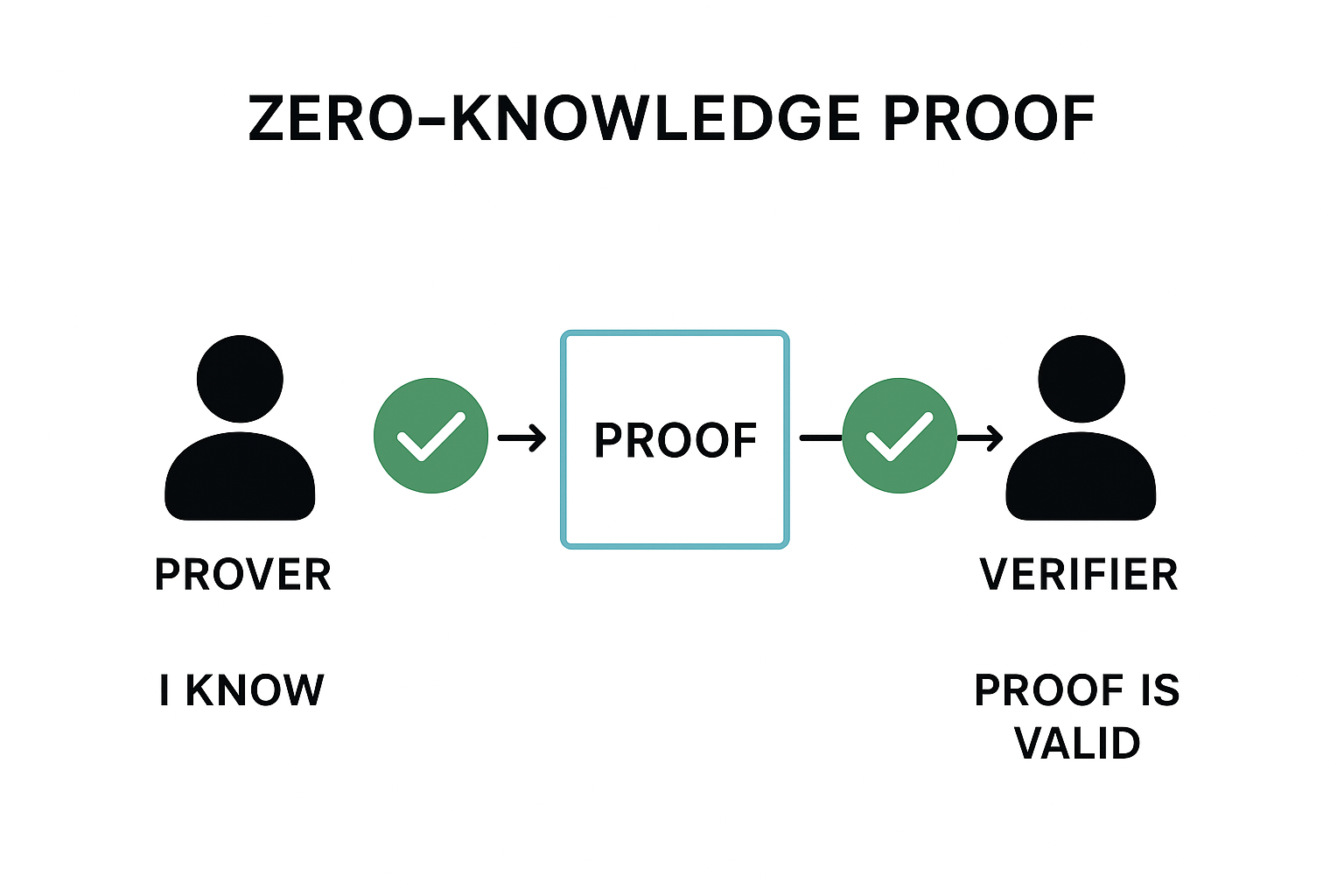
A zero-knowledge proof (ZKP) is a cryptographic technique that allows a prover to convince a verifier that “something is true” without revealing any original information.
In short: ZK lets you prove “I’m following the rules,” without having to disclose “what the rules are.”
This feature is extremely valuable in financial and compliance scenarios:
• You can prove “I passed KYC” without exposing any identity information.
• You can prove “this transaction didn’t exceed regulatory limits,” without revealing the transaction amount.
• A protocol can prove “asset reserves are sufficient,” without exposing internal account structures.
For the first time, ZK gives financial systems: Verifiability + Privacy + Regulatory Compliance
That’s why it’s set to explode in 2024–2025.
Core Idea of ZK: From “Public Computation” to “Proof-Based Computation”
Traditional computation looks like this:
- Provide data
- Provide the computation process
- Produce output
- Verifier re-executes the computation to check correctness
ZK works completely differently:
- Prover performs the computation
- Compresses the computation into “a proof”
- Verifier only checks if the proof is valid, without knowing the inputs or redoing the computation
Advantages include:
• Fast verification (even if the computation itself is complex)
• No need to reveal input data (privacy)
• On-chain verification (ideal for smart contracts)
That’s why ZK is often called foundational technology combining privacy, scalability, and compliance.
Three Core Properties of ZK Proofs
Every ZK technology must meet three essential properties:
- Completeness — If the statement is true, the proof will always pass verification.
- Soundness — If the statement is false, proof cannot be faked to pass verification.
- Zero-Knowledge — The verifier learns nothing about the original data from the proof, only that “the conclusion is correct.”
These properties make ZK reliable for financial scenarios like audits, settlements, and regulatory disclosures.
Two Main Branches of ZK Technology: SNARK vs STARK
Currently, ZKProof frameworks fall into two main categories:
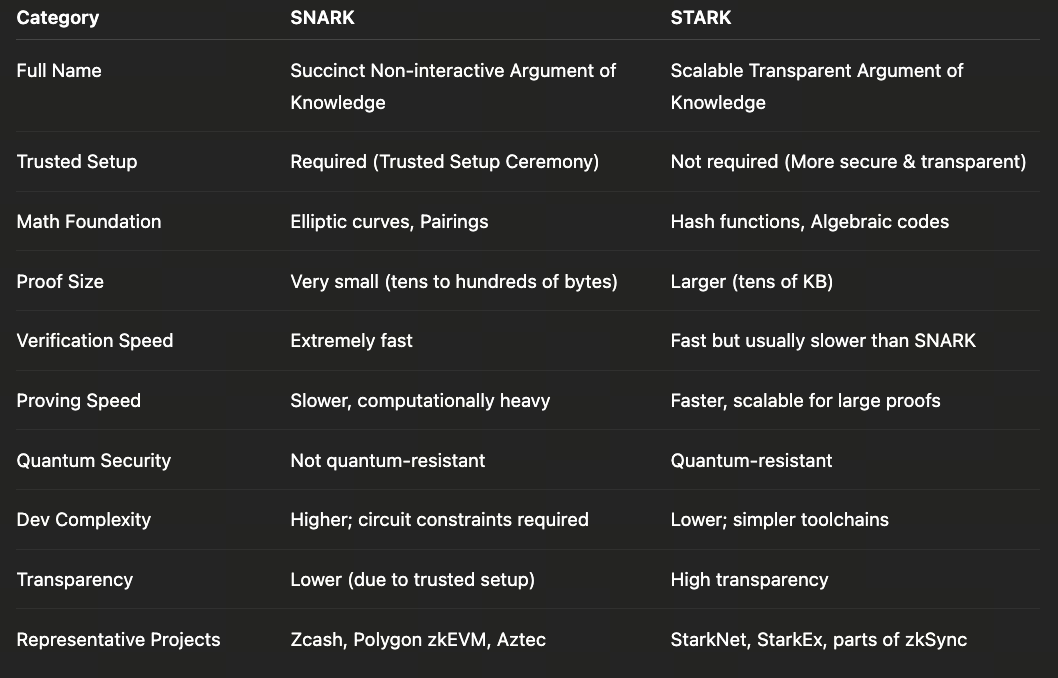
SNARK (zk-SNARK)
Full name: Succinct Non-interactive Argument of Knowledge
Features:
• Small proof size
• Fast verification
• Suitable for mainnets and smart contracts
• Requires trusted setup
• Complex math (elliptic curves, algebraic circuits)
Representative projects: Polygon zkEVM, Zcash, Scroll, Aleo
Use cases:
• High TPS on-chain proofs
• Identity and compliance verification
• ZK Rollups, payment networks
STARK (zk-STARK)
Full name: Scalable Transparent Argument of Knowledge
Features:
• No trusted setup needed (more secure)
• Resistant to quantum attacks
• Larger proof size
• Ideal for large-scale data computation (like DeFi, exchange audits)
Representative projects: Starknet, zkSync (partially uses), Celestia data validation
Use cases:
• Large proof systems
• Enterprise audits
• ZKML (AI model proofs)
How ZK Proofs Are Generated: From Data to Verification
A typical ZK system includes four steps:
- Translate the problem into a mathematical circuit — Example: “Transaction amount does not exceed 10,000 USDT” encoded as an algebraic constraint.
The prover generates a proof based on private inputs — Inputs may include:
○ Identity
○ Transaction amount
○ Account balance
○ Internal company dataThe verifier uses a verification key to check the proof — No need to know the input data, just verify the proof’s validity.
- Verification smart contract runs on-chain — The proof is compressed into a small enough package for on-chain validation.
ZK Isn’t About “Hiding Everything”. It’s About Hiding Unnecessary Information
A common misconception is: “ZK prevents regulators from seeing data.”
Actually, it’s quite the opposite. ZK enables systems to:
• Be verifiable for regulatory audits
• Maintain privacy for the general public
• Protect commercial secrets for institutions
• Minimize exposure to counterparties
For example, controlled privacy models may include:
• Audit view keys
• Judicially authorized decryption mechanisms
• Selective disclosure
This makes ZK one of the few “regulator-friendly privacy technologies” in finance.
Why Is ZK Especially Suited for Financial and Compliance Scenarios?
Financial operations require verification, no disclosure of details
For example:
• KYC status
• Sufficient assets
• Regulatory risk exposure
• Transaction limit compliance
All can be achieved with ZK.
Privacy protection is becoming a global regulatory mandate
For example:
• EU GDPR
• MiCA privacy exemptions
• US GLBA (Gramm-Leach-Bliley Act)
ZK helps businesses “protect users compliantly.”
Auditability + privacy are possible together for the first time with ZK
Other privacy tech struggles with this balance.
Summary: ZK Is the Foundation of Future Compliant Finance
By completing this lesson, you’ve learned:
• The basic definition and value of ZK
• The SNARK / STARK branches
• How ZK operates
• Why ZK is becoming a key technology for financial compliance
It’s not just a privacy tool, it’s the “security proof layer” enabling Web3 and global financial systems to work together.
In the next lesson, we’ll move into real-world applications: case studies and architecture design of ZK in compliance, audit, identity verification, and private transactions.