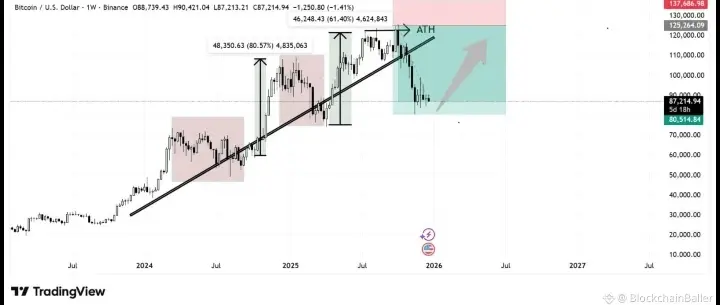
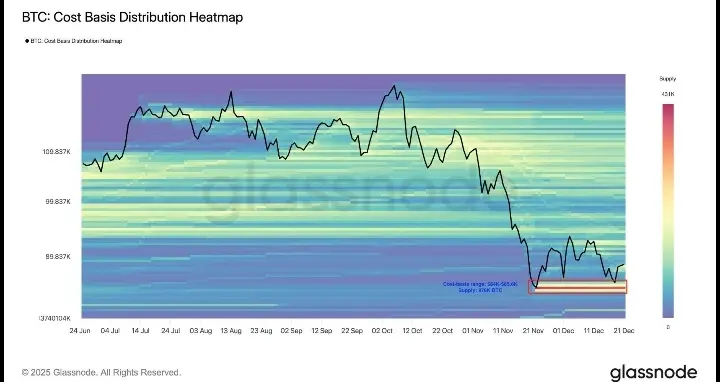
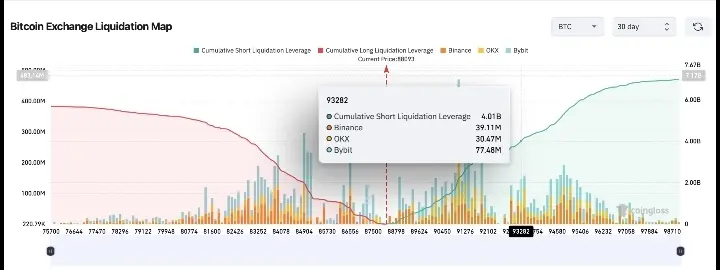
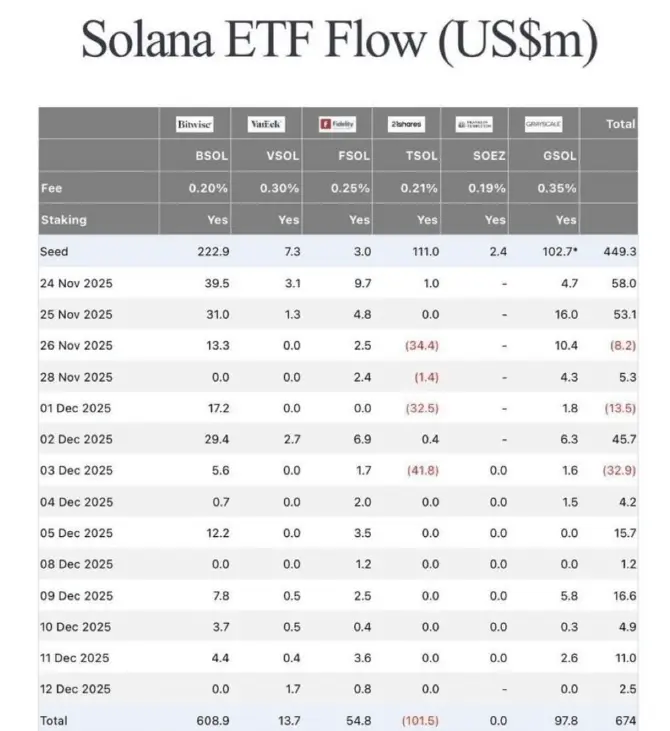
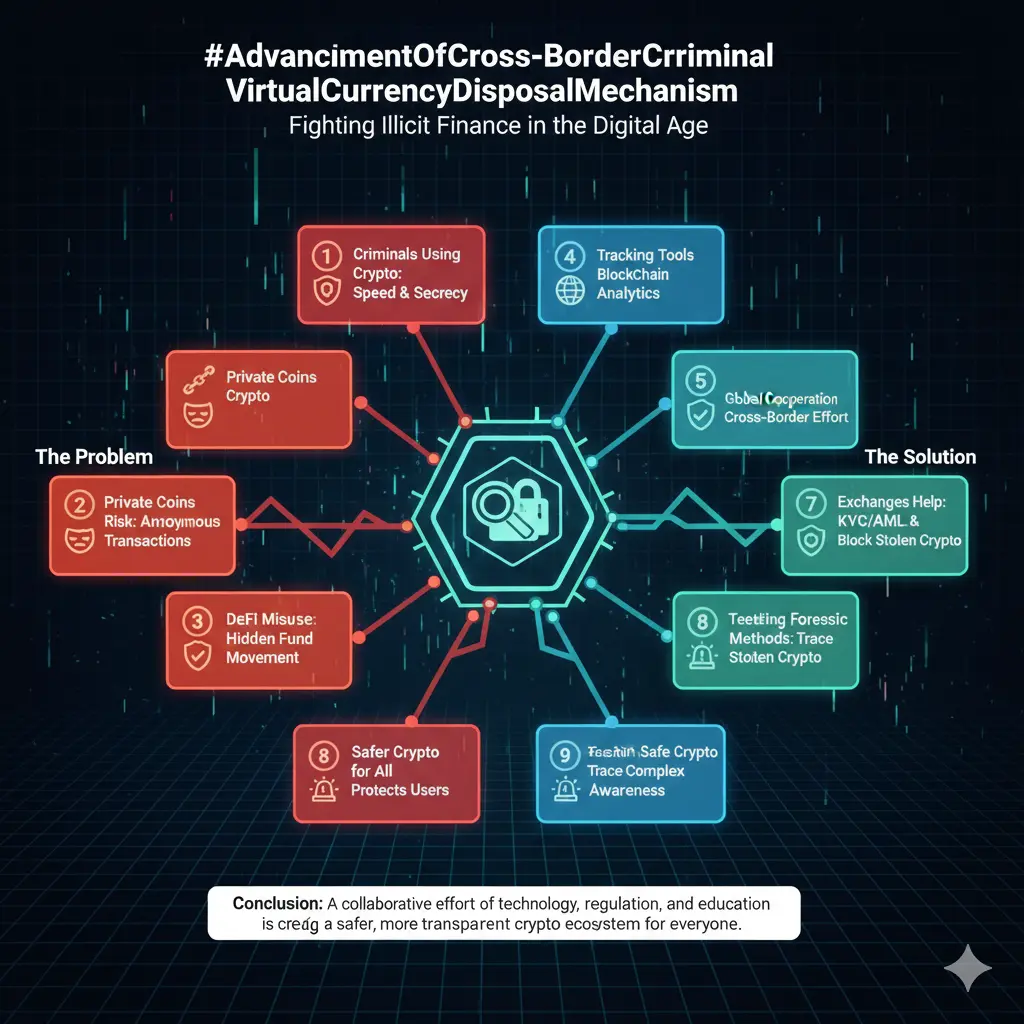
#发帖赢代币NIGHT Midnight: The Fourth Generation Blockchain, Reshaping the Future of Web3
Midnight Fourth Generation Blockchain (Cryptocurrency)
Midnight is based on scientific research, aiming to address issues such as insufficient privacy in existing blockchains, regulatory automation difficulties, identity verification inconveniences, and collaboration dilemmas. It promotes large-scale global adoption of blockchain technology and creates a new future of compliance, data protection, and free economy through innovative technology.
Evolution of the Fourth Generation Blockchain
First Generation: Bitcoin — solved the problem of decentralized value transfer, removing intermediaries.
Second Generation: Ethereum — introduced smart contracts, enhancing blockchain programmability and application diversity.
Third Generation: Cardano — innovated and partially implemented solutions for scalability, interoperability, and governance.
Midnight — Focuses on three major issues not fully resolved by the previous three generations: "Rational Privacy," "Identity," and "Cooperation."
Midnight’s Three Pillars
1. Rational Privacy
Historically, blockchains emphasized full transparency, but real-world needs require "selective disclosure."
Midnight innovatively integrates technologies such as zero-knowledge proof, Kachina, and Nightstream, enabling users to choose when and to whom to disclose identity, assets, and sensitive data.
Supports on-chain and off-chain privacy, utilizing hardware acceleration (tensor codes) and fully homomorphic encryption to improve efficiency and scalability.
Kachina Technology: An innovative architecture designed specifically for privacy protection in blockchain and smart contracts, applied to Cardano-related Midnight public chain projects. Kachina is a virtual machine (Kachina VM, KVM) that incorporates ZK proofs into smart contract design, enabling "data protection and compliant audit" for on-chain transactions and contract execution. Nightstream: Uses lattice-based cryptography, designed to resist quantum computers, combined with ZK proofs, FHE, Tensor Codes (GPU-accelerated algorithms), and scalable Layer 2 blockchain integration.
2. Identity (Decentralized Identity DID)
Web3 needs to solve the challenge of securely proving identity. DID standards allow individuals, AI, and objects to obtain globally unique and verifiable identities.
By combining rational privacy and identity, identity verification and privacy become programmable and modular, giving users full control over their data disclosure pace.
Enables regulatory automation (e.g., automated KYC and compliance processes).
3. Cooperation (Large-scale Adoption Protocol)
Midnight rejects the unfair token issuance mechanisms of traditional "Ponzanomics" (Ponzi economics VC models). Instead, it uses methods like "Glacier Airdrops," "Mining," and "Lost and Found" to fairly distribute tokens across eight ecosystems (BTC, ETH, ADA, SOL, BSC, AVAX, XRP, BAT).
Dual-token mechanism: Night (used for governance and value storage) and Dust (generated by Night, used as utility tokens for payments and private operations), balancing asset stability and appreciation.
Network effects: Features like "Capacity Exchange" and "Cooperative Consensus" promote collaboration and liquidity among multi-chain assets and validators, enabling true cross-chain and scalable solutions.
Emphasizes the "Intention Layer": Future DeFi and general web services will move toward "declaring intentions and automatic network execution." Midnight’s privacy architecture ensures that even if intentions are on-chain, sensitive information remains confidential.
Summary
Midnight is the latest generation blockchain combining academic research, cutting-edge cryptography, and practical engineering.
It emphasizes "privacy, identity, sovereignty, compliance, and cooperation," aiming to promote large-scale real-world adoption of Web3 and re-empower individual digital sovereignty.
Midnight Fourth Generation Blockchain (Cryptocurrency)
Midnight is based on scientific research, aiming to address issues such as insufficient privacy in existing blockchains, regulatory automation difficulties, identity verification inconveniences, and collaboration dilemmas. It promotes large-scale global adoption of blockchain technology and creates a new future of compliance, data protection, and free economy through innovative technology.
Evolution of the Fourth Generation Blockchain
First Generation: Bitcoin — solved the problem of decentralized value transfer, removing intermediaries.
Second Generation: Ethereum — introduced smart contracts, enhancing blockchain programmability and application diversity.
Third Generation: Cardano — innovated and partially implemented solutions for scalability, interoperability, and governance.
Midnight — Focuses on three major issues not fully resolved by the previous three generations: "Rational Privacy," "Identity," and "Cooperation."
Midnight’s Three Pillars
1. Rational Privacy
Historically, blockchains emphasized full transparency, but real-world needs require "selective disclosure."
Midnight innovatively integrates technologies such as zero-knowledge proof, Kachina, and Nightstream, enabling users to choose when and to whom to disclose identity, assets, and sensitive data.
Supports on-chain and off-chain privacy, utilizing hardware acceleration (tensor codes) and fully homomorphic encryption to improve efficiency and scalability.
Kachina Technology: An innovative architecture designed specifically for privacy protection in blockchain and smart contracts, applied to Cardano-related Midnight public chain projects. Kachina is a virtual machine (Kachina VM, KVM) that incorporates ZK proofs into smart contract design, enabling "data protection and compliant audit" for on-chain transactions and contract execution. Nightstream: Uses lattice-based cryptography, designed to resist quantum computers, combined with ZK proofs, FHE, Tensor Codes (GPU-accelerated algorithms), and scalable Layer 2 blockchain integration.
2. Identity (Decentralized Identity DID)
Web3 needs to solve the challenge of securely proving identity. DID standards allow individuals, AI, and objects to obtain globally unique and verifiable identities.
By combining rational privacy and identity, identity verification and privacy become programmable and modular, giving users full control over their data disclosure pace.
Enables regulatory automation (e.g., automated KYC and compliance processes).
3. Cooperation (Large-scale Adoption Protocol)
Midnight rejects the unfair token issuance mechanisms of traditional "Ponzanomics" (Ponzi economics VC models). Instead, it uses methods like "Glacier Airdrops," "Mining," and "Lost and Found" to fairly distribute tokens across eight ecosystems (BTC, ETH, ADA, SOL, BSC, AVAX, XRP, BAT).
Dual-token mechanism: Night (used for governance and value storage) and Dust (generated by Night, used as utility tokens for payments and private operations), balancing asset stability and appreciation.
Network effects: Features like "Capacity Exchange" and "Cooperative Consensus" promote collaboration and liquidity among multi-chain assets and validators, enabling true cross-chain and scalable solutions.
Emphasizes the "Intention Layer": Future DeFi and general web services will move toward "declaring intentions and automatic network execution." Midnight’s privacy architecture ensures that even if intentions are on-chain, sensitive information remains confidential.
Summary
Midnight is the latest generation blockchain combining academic research, cutting-edge cryptography, and practical engineering.
It emphasizes "privacy, identity, sovereignty, compliance, and cooperation," aiming to promote large-scale real-world adoption of Web3 and re-empower individual digital sovereignty.